20 minute read time
Increasing cloud adoption and the rising risk of cyberattacks create new challenges for enterprise IT teams, who must ensure the online accessibility and absolute security of an increasingly distributed, remote workforce. Discover what SASE is and why enterprises are turning to this new security framework to meet those needs.
SASE explained
How does SASE work?
6 key benefits of SASE
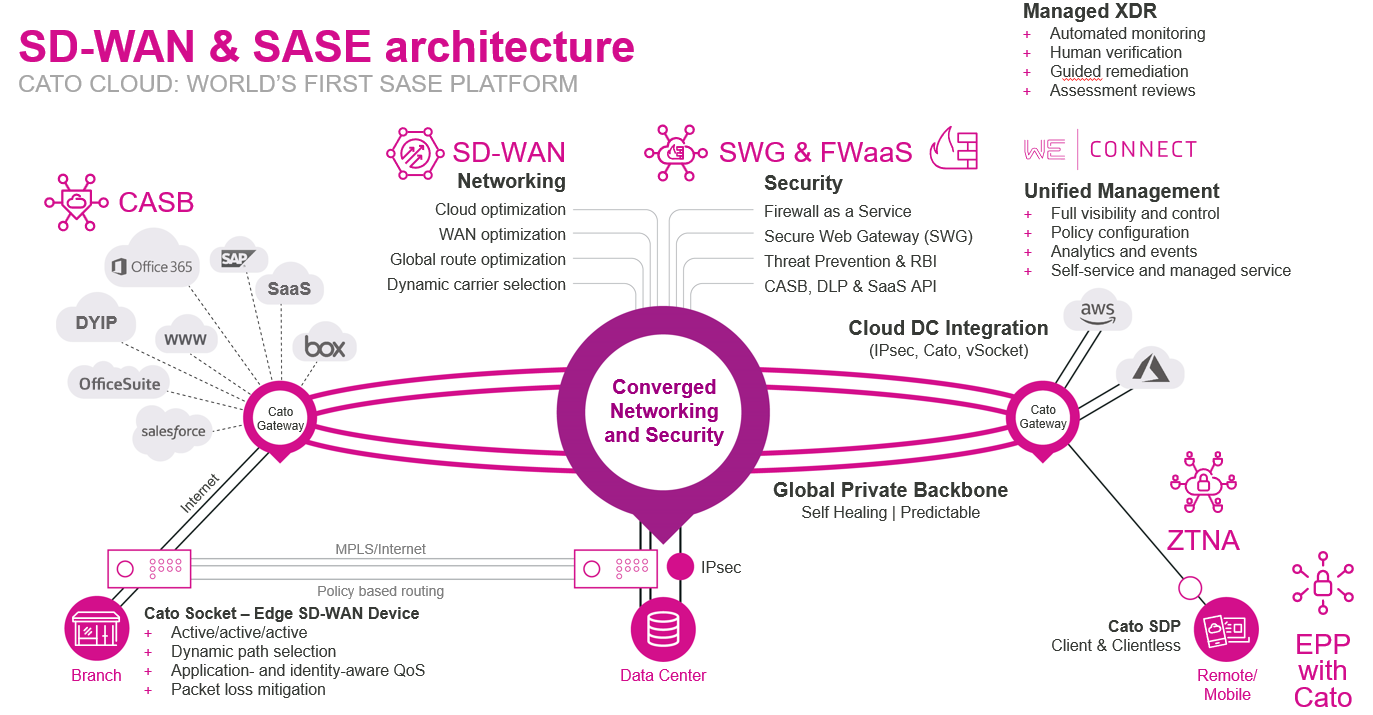
What does a true SASE architecture look like?
Tips for implementing SASE
6 criteria for selecting an SD-WAN service provider
SASE from Windstream Enterprise
SASE Case Studies
SASE explained
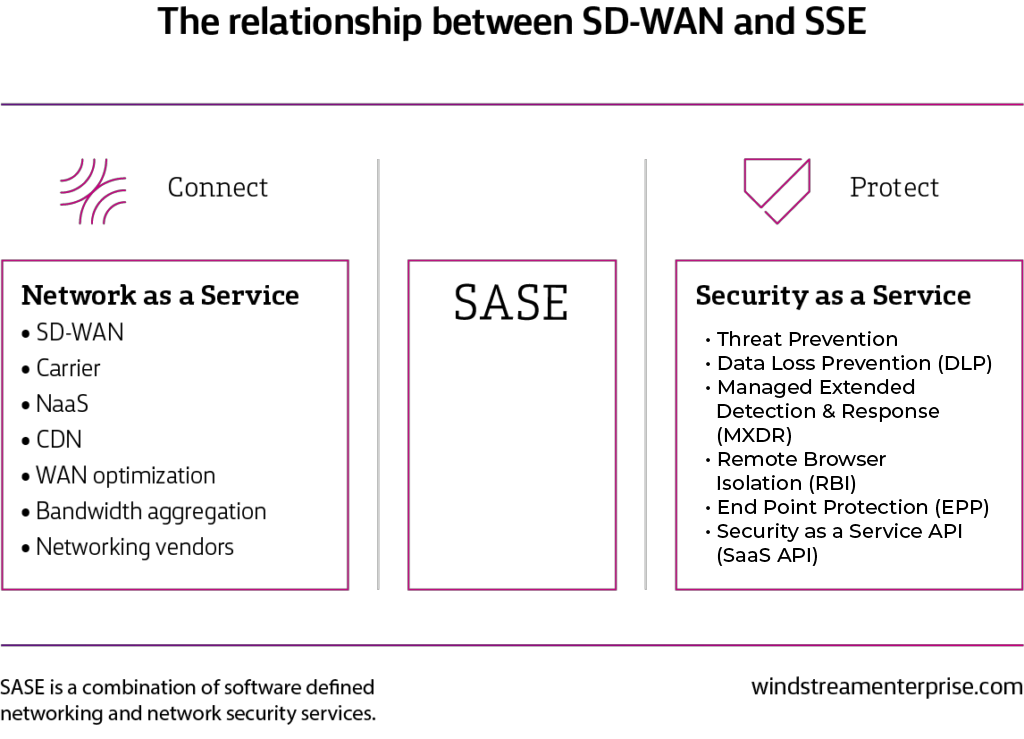
Secure Access Service Edge (SASE) is a cloud-native network and security framework that provides users with secure cloud access to applications, data and services and protects an organization’s data and systems from unwanted access.
This architecture integrates “network as a service” with “network security as a service,” resulting in unified, secure connectivity that’s available anytime, anywhere.
Gartner’s SASE definition
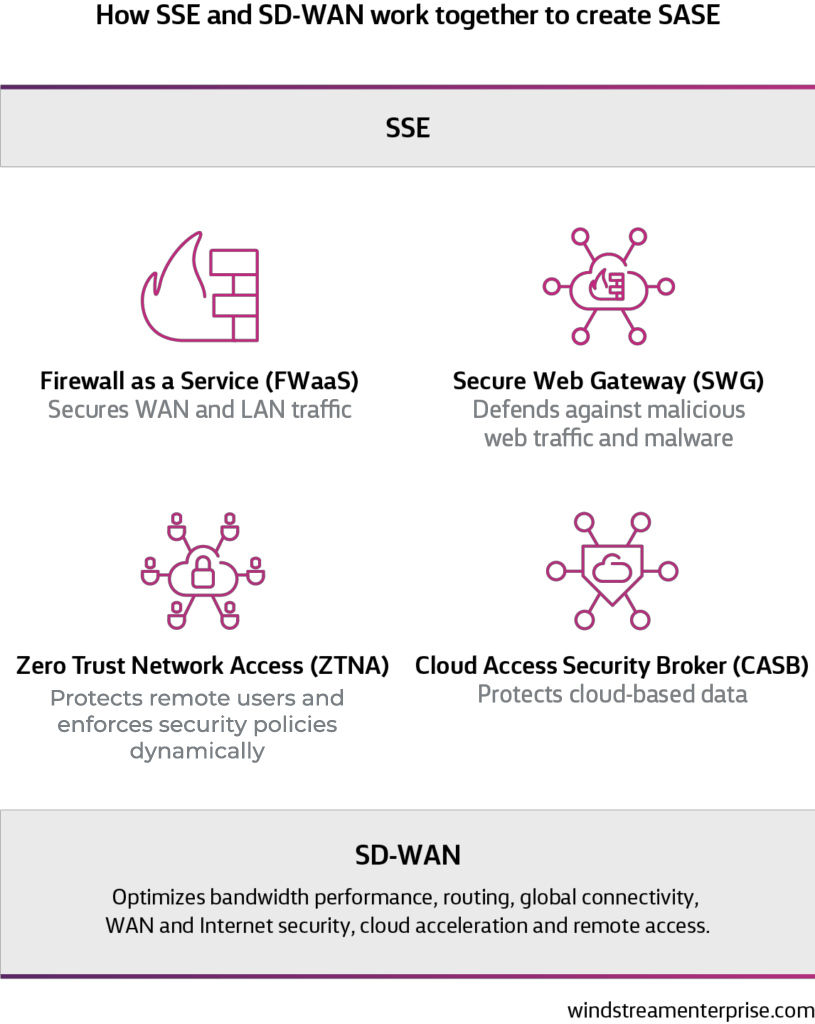
According to Gartner, SASE is an emerging offering combining comprehensive networking and security functions—such as software-defined wide-area networking (SD-WAN), Firewall as a Service (FWaaS), Secure Web Gateway (SWG), Cloud Access Security Broker (CASB) and Zero Trust Network Access (ZTNA)—to support the dynamic secure access needs of organizations.1
Why is SASE necessary?
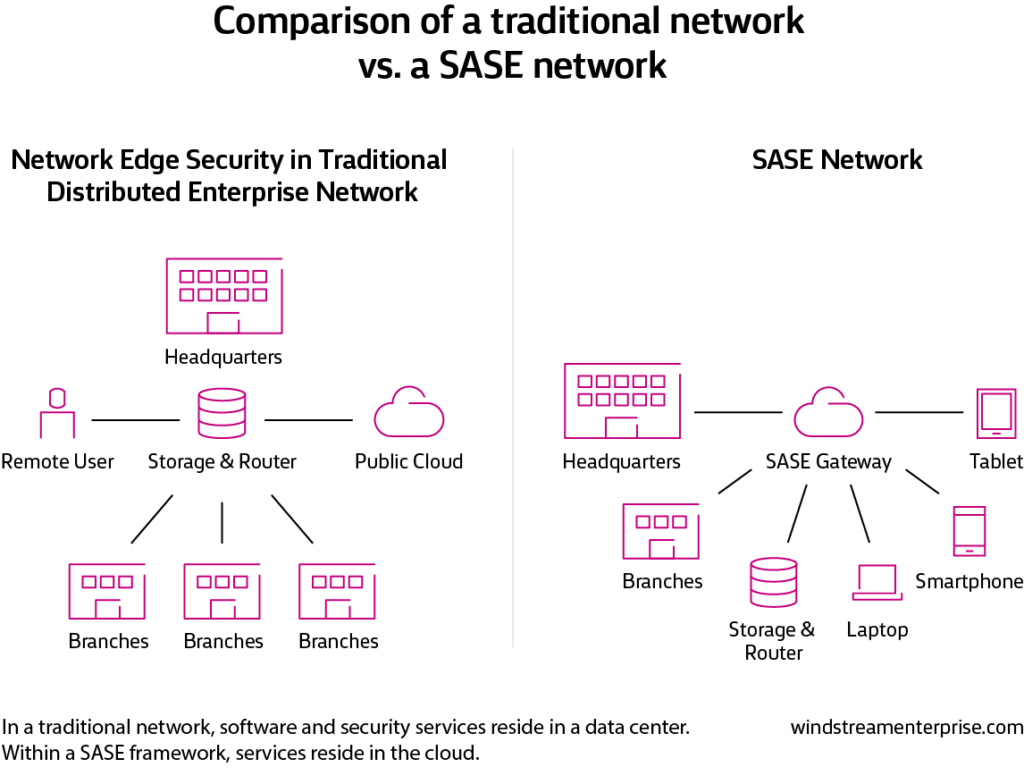
As more organizations pursue digital transformation, they are incorporating the public Internet to support cloud-native applications and services as an alternative to investing in additional, costly on-premises infrastructures. That’s led to an increase in application traffic traveling beyond the traditional corporate perimeter—and beyond the reach of traditional network security measures. SASE offers agile, robust security to secure traffic at any endpoint, anywhere.
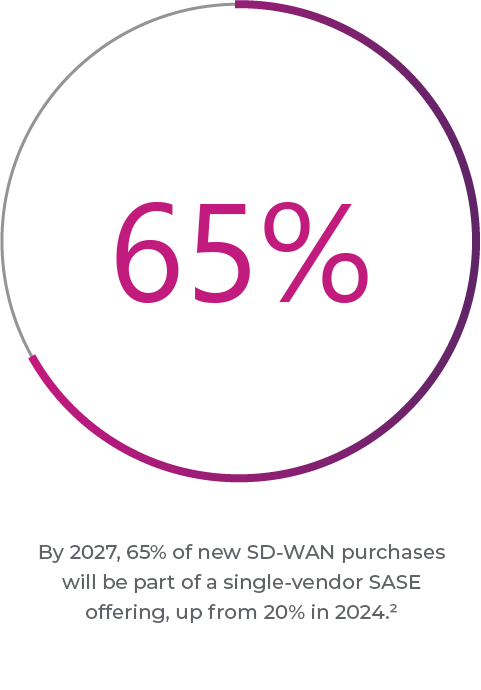
3 drivers of SASE adoption
Enterprises are adopting SASE for a number of reasons, including:
1. The rise of remote work:
The pandemic—and the rapid shift to remote work that followed—has led to remote workers logging on from home or any public WiFi hotspot using a mix of personal and company devices.
2. The decentralization of computing:
To improve response times and optimize bandwidth, data storage and computing has moved closer to the edge of the network where the data is generated and consumed.
3. The dramatic rise in cyberattacks:
As reported in SDxCentral, 86% of organizations surveyed expect to be impacted by a cyberattack within a year. In a hub-and-spoke network model, security solutions are fragmented among physical locations, cloud resources and mobile users, making it a challenge to monitor and remediate ever-increasing cybersecurity incidents. Additionally, security insurance for ransomware attacks has become prohibitively expensive.
To dive deeper into the migration to SASE in the business network, see the whitepaper The unification of network and security
How do you know when it’s time to switch to SASE?
How do you know when it’s time to leave your legacy solutions behind and begin the migration to SASE? Here are four signs to look out for:
Losing agility and flexibility
Your current network is no longer nimble enough to evolve with your organization’s future-proofing initiatives, such as supporting new cloud workloads, addressing a remote workforce and accommodating rapid expansion.
Increasing security vulnerabilities
Your security solutions are fragmented among physical locations, cloud resources and mobile users, and it’s becoming a challenge to monitor and remediate cybersecurity incidents across all perimeters. You fear your organization will fall victim to the next cyberattack.
Degrading app performance
Your lagging business applications are starting to impact your employees’ productivity. With secure, reliable, low-latency connectivity to cloud and data center applications, your employees can always access the tools they need for maximum efficiency.
Lacking visibility and control
You can’t control what you can’t see. Limited visibility into applications and bandwidth makes it hard to control and manage application performance and security.
- Are you ready for SASE? Take our short assessment questionnaire