Top 5 tips to mitigate unified communications security risks
8-minute read time
A cloud-based unified communications (UC) solution offers a range of benefits to enterprises—from higher employee and customer satisfaction, to greater productivity from seamless collaboration and a reduced burden on IT. However, it also presents security and quality of service (QoS) challenges for IT departments if not managed correctly.
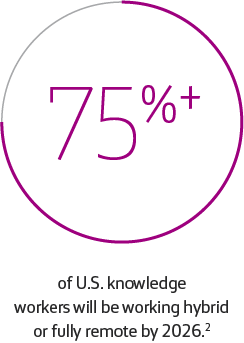
Since a UC solution conveys a wide range of information in the cloud using broadband networks that are open, it can expose enterprise communications infrastructure, services and applications to a wide range of threats.
We’ll explore ways to mitigate these threats to Unified Communications as a Service (UCaaS), the most common enterprise cloud-based UC solution today.
Why unified communications security challenges exist
With mobility and work from anywhere becoming more popular, UCaaS adoption has increased. From an IT perspective, that means the organizational network perimeter is no longer confined to a specific location. Businesses are doing more business. As a result, their data may no longer be as safe as it was in a closed network—while their network performance is bound to suffer.
Traditionally, hub-and-spoke networks and their security architecture were based on closed network models that served stationary endpoints from data centers. Today, security must extend beyond the data center to secure endpoints everywhere. To accomplish this, security policies need to be managed at the identity and application layers.
The 5 biggest security threats to UCaaS
All organizations fear cybersecurity attacks and threats, regardless of their industry. Learn about the different types of threats your business might face—and how to defend against them.

Phishing
Emails are sent to users enticing them to click on a URL and fill out a web form.
The risk
Employees may unwittingly divulge sensitive company information.
How to mitigate
Identify network anomalies and security vulnerabilities by inspecting website access for malicious domains, as well as WAN and Internet traffic, for dangerous files embedded within attachments or suspicious hyperlinks.
Ransomware
A type of malicious software designed to block access to a computer system by encrypting a cyber victim’s files.
The risk
It costs the enterprise large sums of money to unlock critical company data and resources.
How to mitigate
Incorporate secure access service edge (SASE) elements into the network, such as:
- Secure web gateways (SWG)
- Zero trust network access (ZTNA)
- Security broker (CASB) with data loss prevention (DLP)
Distributed denial-of-service (DDoS) attack
When a cybercriminal attempts to make it impossible for an online service to be delivered by overwhelming it with traffic from multiple sources.
The risk
It can paralyze business transactions and lead to massive losses of revenue.
How to mitigate
CASB components that extend DDoS protection to the edge.
Third-party malware
If malware is included in third-party software, it can potentially lead to network intrusions and vulnerabilities.
The risk
The company can’t fix the issues due to a lack of visibility into that software, resulting in costly damages to business functions and services.
How to mitigate
CASB and next-generation firewalls (NGFWs) offer a point solution for governing cloud application access and avoiding shadow IT.
Insecure cloud storage
Can result in attackers gaining access to data stored in the cloud and stealing confidential information.
The risk
Stolen information can be bought and sold by bad actors, leading to loss of corporate reputation and potential liability.
How to mitigate
A secure access service edge (SASE) framework uses security service edge (SSE) components to secure storage, transmission and information sharing.
Essential security requirements in a UCaaS solution
To reduce cyberthreats in your cloud-based unified communications solution, make sure you work with a provider that understands UC security best practices. It’ll save you from disjointed, point-based solutions that complicate management and lead to potential network vulnerabilities. By implementing UC as a service, your provider can keep your security posture up to date—saving you and your team time and effort.
Regulatory compliance
Most companies are required to follow some form of industry regulation and compliance standard. Here are two key standards your provider should be certified to meet.
HIPAA
Your communications infrastructure must comply with Health Insurance Portability and Accountability Act (HIPAA) requirements if your organization is involved in healthcare. Under HIPAA, healthcare organizations are required to protect the integrity and security of protected health information, including protection from unauthorized access or disclosure.
SOC
In the financial services industry, meeting System and Organization Controls (SOC) requirements is key. The American Institute of Certified Public Accountants (AICPA) defines SOC as a suite of reports produced during an audit. Specifically, SOC 2 focuses on non-financial reporting controls related to security, availability, processing integrity, confidentiality and privacy. Reports in SOC 2 are private, but SOC 3 are open to the public on an organization’s website.
SSE components
As a subset of SASE, SSE delivers security capabilities across a distributed enterprise from a scalable, cloud-based platform.
- ZTNA secures application access for users with a zero-trust policy, where application access dynamically adjusts based on user identity, location, device type and more.
- CASB applies security policies as users access cloud-based resources to protect against cloud security risks, comply with data privacy regulations and enforce corporate security policies.
- SWG protects users against malware, phishing and other web-borne threats. Because it extends protection to all users at all locations, it eliminates the need to maintain policies across multiple point solutions.
- Firewall as a service (FWaaS) is a next-generation firewall that eliminates the appliance form factor, making network security capabilities, such as URL filtering, intrusion prevention system (IPS), next-generation anti-malware (NGAM) and managed detection & response (MDR) available everywhere.
Resilient connectivity
Secure communications start with intelligent, reliable connectivity.
- Software-defined wide area networking (SD-WAN) routes traffic dynamically across distributed branches and remote locations. It creates a virtual WAN that connects remote branches and locations no matter what type of connection, access point, or carrier they use. When combined with the SSE components listed above, SD-WAN enables SASE to ensure users and devices have secure cloud access to applications, data and services at any location.
Ready to improve unified communications security?
The explosion of remote work and cloud adoption gives enterprises more opportunities than ever to create new UCaaS success stories by enabling richer employee and customer experiences. But many businesses don’t have the right tools to safeguard their data. Organizations can’t fully protect themselves with solutions designed for perimeter-based networks. That’s why it’s critical to pair any UCaaS solution with security that extends beyond the perimeter to the endpoints themselves—regardless of device or location.
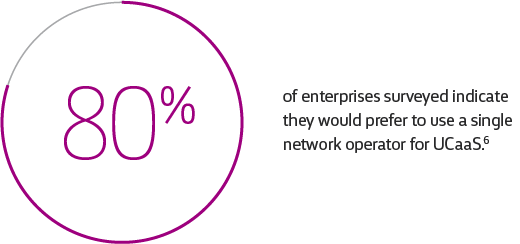
Secure UCaaS from Windstream Enterprise
Cloud UC and security solutions from Windstream Enterprise help employees connect and collaborate securely with customers and each other. With a compliant, award-winning and customer-verified UCaaS solution that includes SD-WAN and SASE, planned and deployed by our team of specialists and managed from a single pane of glass, your organization can drive productivity and engagement like never before.
To find out more about UCaaS from Windstream Enterprise, visit the unified communications solutions page.
Citations
- Atwal, Griffen, Padhi & Banerjee: “Forecast Analysis: Knowledge Employees, Hybrid, Fully Remote and On-Site Work Styles, Worldwide.” Gartner. Jan. 6, 2023.